CISA Publishes KEV Submission 60-day ICR Notice
Today, CISA published a 60-day information collection request notice in the Federal Register (89 FR 14896-14897) for “Actively Exploited Vulnerability Submission Form”. The dedicated form on the CISA website will allow for external reporting of vulnerabilities that the reporting entity believe to be Known Exploited Vulnerabilities (KEV) eligible.
Background
CISA began publishing their Known Exploited Vulnerabilities (KEV) catalog in 2021. There are currently 1082 vulnerabilities listed. The earliest listing shown today is November 3rd, 2021, but an earlier version of the catalog showed a first date of March 3rd, 2021.
Binding Operational Directive 21 is the governing document for the KEV catalog. That document provides the three criteria that CISA is using to determine which vulnerabilities should be listed in the catalog:
Has an assigned Common Vulnerabilities and Exposures (CVE) ID.
There is reliable evidence that the vulnerability has been actively exploited in the wild.
There is a clear remediation action for the vulnerability, such as a vendor provided update.
CISA has not said much about how they have identified vulnerabilities that meet their undefined criteria for listing vulnerabilities in the KEV catalog.
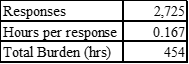
Burden Estimate
Today’s notice provides the following burden estimate:
CISA estimates that the ICR will cost respondents $37,596 per year, probably based on an average salary for the person submitting the KEV data, since CISA is reporting $0 out-of-pocket expenses for respondents. The governmental costs of receiving and processing the KEV submissions is estimated to be $145,924.
As is typical for ICR notices, CISA has not included a link to the on-line form that they expect submitters to use. They do note that interested personnel can request a ‘developmental digital copy’ of the form is available from Christopher Murray, christopher.murray@cisa.dhs.gov.
Public Comments
CISA is soliciting public comments on this ICR. Comments may be submitted via the Federal eRulemaking Portal (www.Regulations.gov; Docket #CISA-2024-0008) comments should be submitted by April 29th, 2024.
Commentary
There are two things missing from this ICR notice. First is any reference to Binding Operational Directive 22-01 which establishes the purpose of the KEV catalog. Second, and probably more important for public consideration of the ICR for the purposes of comments, is a listing of the criteria that CISA uses to evaluate a vulnerability for consideration of listing in the KEV compatibility.
The more important thing that catches my attention, however, is that CISA is expecting to receive 2,725 submissions each year for proposed for listing in the KEV catalog. With only 1082 currently listed (since 2021) vulnerabilities, CISA looks to be greatly expanding the size of this catalog.